Software Maintenance Software maintenance is the process where after the software been released to end user, there will be:-
- Abug reports about the software
- Changes that need to be done to suit one class of user.
- A few adjustments on the software for another corporate company that have seen unexpected benefits on the software.
This is among of the work that can be called software maintenance.
Software maintenance and support.
• Ongoing activities to change and support the software after it is in operation.
-No degrade or require periodic maintenance.
-Software continually evolving.
• For example :-
- Correcting defects
- Adapting application according to the business environment.
- Implementing enhancement according to the request of the shareholder
-
Support the user as they using the application in their personal and business.
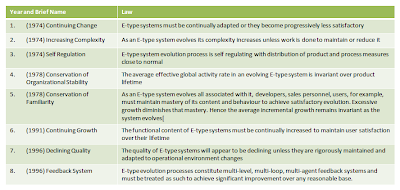
Lehman’s law of Software Engineering.
the Laws of Software Engineering a series of laws that Lehman and Belady formulated starting in 1974 with respect to Software evolution. The laws describe a balance between forces driving new developments on one hand, and forces that slow down progress on the other hand.
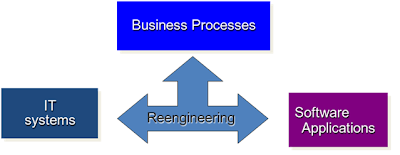
'Re-engineering' is a set of activities that are carried out to re-structure a legacy system to a new system with better functionalities and conform to the hardware and software quality constraint. Reengineering may begin with a Business Process Reengineering (BPR) before move on to software reengineering.
General reengineering principles
1. Inspect the product
2. Inspect the structure of the product, rebuild if it is weak, remodel if it is structurally sound
3. Understand how well the original was built before you rebuild
4. If you begin rebuild, use only the best methods, tools, resources etc
5. Be disciplined about it – use practices that will result in high quality
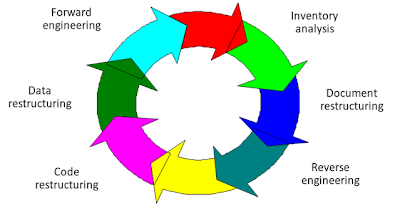
Inventory analysis
An inventory list that contain information that provide description for example:-
– name of the application
– year it was originally created
– number of substantive changes made to it
– total effort applied to make these changes
– date of last substantive change
– effort applied to make the last change
– system(s) in which it resides
– applications to which it interfaces
Document restructuring.
- Creating documentation is far too time consuming. If the system works, we’ll live with what we have. In some cases, this is the correct approach.
- Documentation must be updated, but we have limited resources. We’ll use a “document when touched” approach. It may not be necessary to fully redocument an application.
- The system is business critical and must be fully redocumented. Even in this case, an intelligent approach is to reduce documentation to an essential minimum.
Reverse Engineering
• Recreate design and specification information from the source code
• The process of analyzing a program in an effort to create a representation of the program at higher level of abstraction than source code.
Code structuring & restructuring.
Code structuring.
• Source code is analyzed using a restructuring tool.
• Poorly design code segments are redesigned
• Violations of structured programming constructs are noted and code is then restructured (this can be done automatically)
• The resultant restructured code is reviewed and tested to ensure that no anomalies have been introduced
• Internal code documentation is updated
Code restructuring.
• Activities:
1. Interpreting the source code and representing it internally
2. Simplifying the internal representation
3. Regenerating structured code
Data restructuring.
• Data restructuring is a full scale reengineering activity. In most cases, data restructuring begins with a reverse engineering activity.
o Current data architecture is dissected and necessary data models are defined (Chapter 9).
o Data objects and attributes are identified, and existing data structures are reviewed for quality.
o When data structure is weak, the data are reengineered.
• Because data architecture has a strong influence on program architecture and the algorithms that populate it, changes to the data will invariably result in either architectural or code-level changes.
Forward engineering.
• Forward engineering process applies software engineering principles, concepts, and methods to re-create an existing application.
• In most cases, forward engineering does not simply create a modern equivalent of an older program.
• Rather, new user and technology requirements are integrated into the reengineering effort.
• Capabilities of the older program may be extended too







